One platform to source and operate any device "as a service"
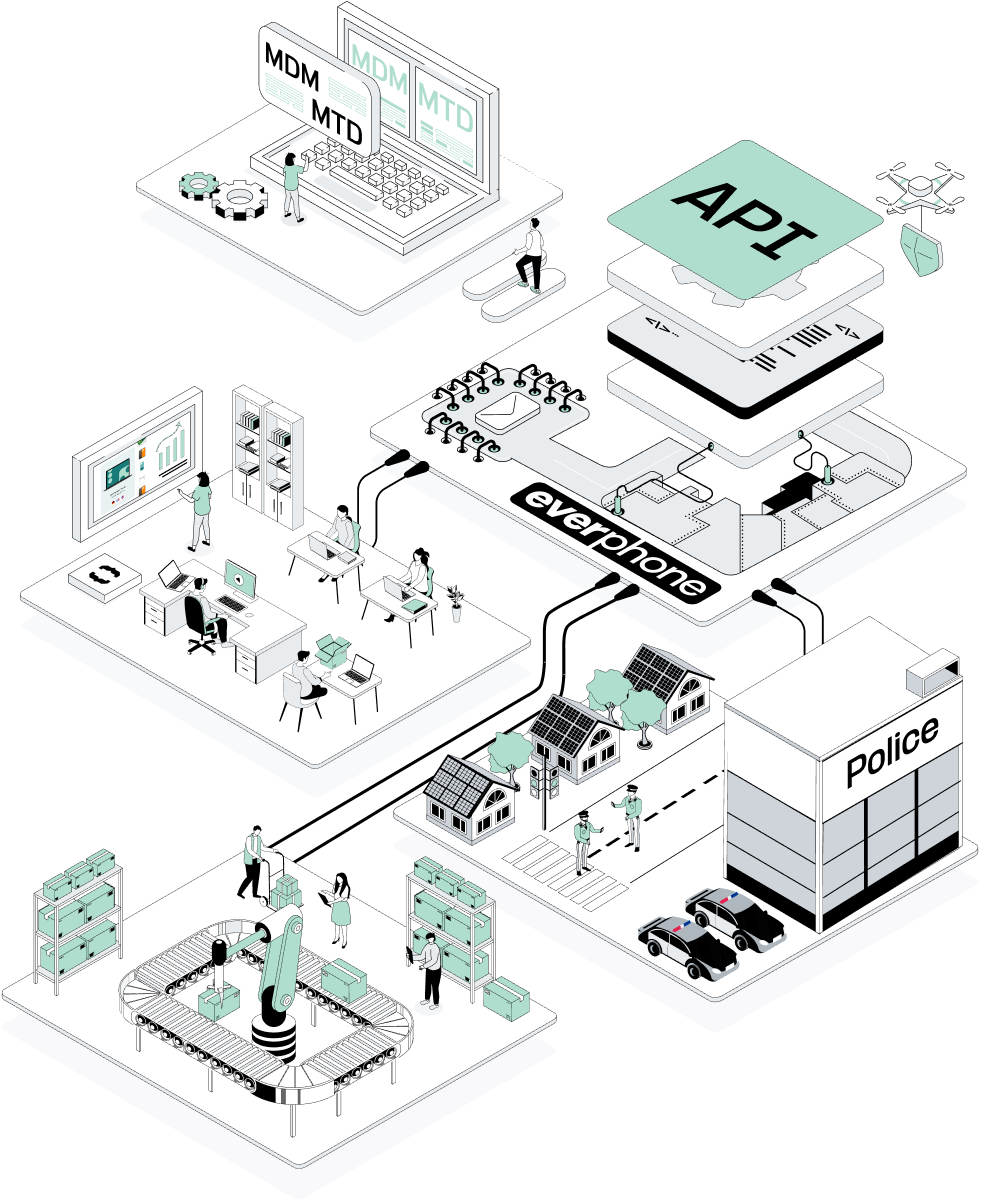
Under pressure: IT and procurement teams
-
More devices
Mobile fleets grow both in numbers and model variation. -
More use-cases
More users, more apps, more workflows add to the complexity. -
More compliance
Privacy and security regulations must be fulfilled. -
More expectations
Users expect quick solutions, if a device has issues.
Procure, stage, deploy, and return devices
with the Everphone platform
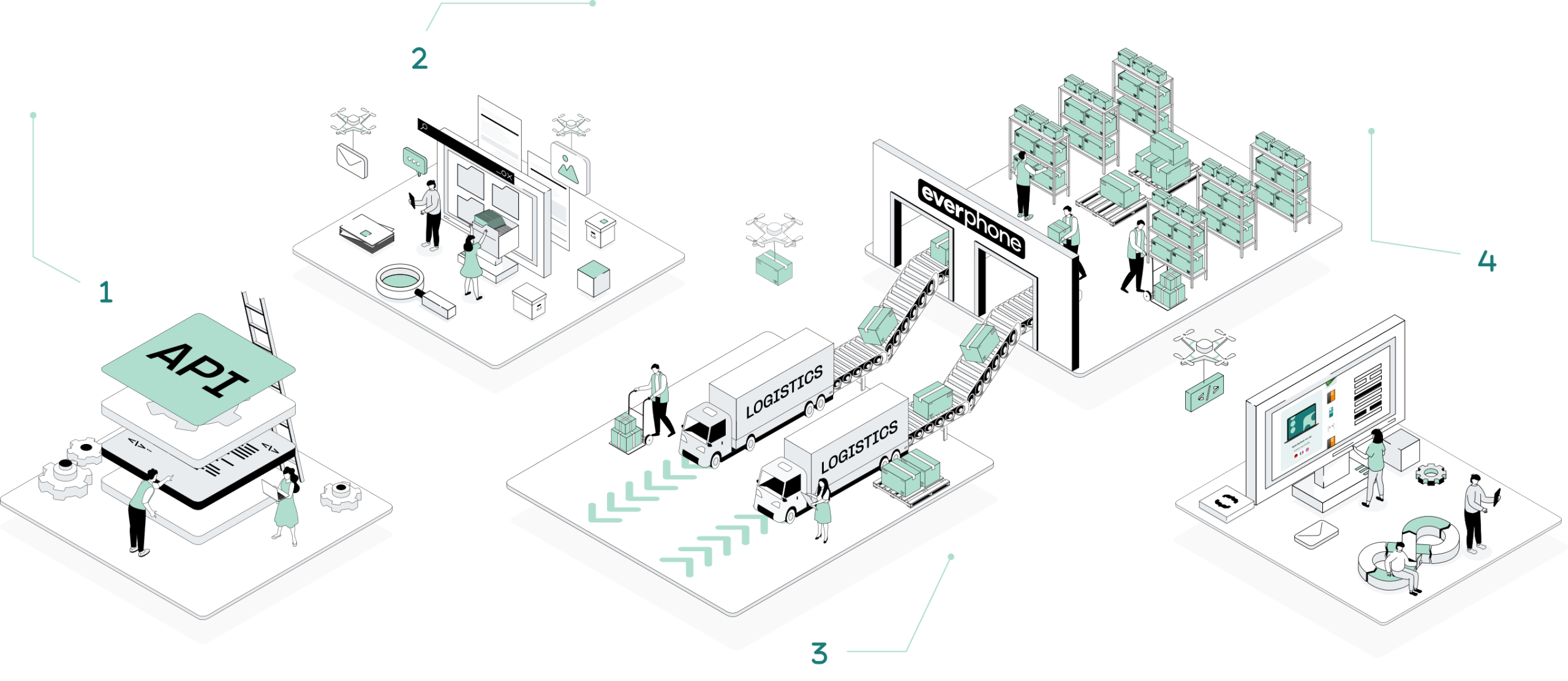
API integration
Everphone stages and integrates all rental devices and connects them to your software stack (MDM/ITSM).Compliance
Everphone rental devices are compliant with regulations such as GDPR and NIS. Private user data is separated. We also give a full audit trail and CO2 documentation.Two-way handling
Everphone delivers and retrieves devices in direct contact with the end user. No more return tasks for your IT team, no more unused legacy devices in your storage.Scale up or down
We centralize and automize device handling for your national teams and abroad. Scale up (or down) according to your needs and development.1. API Integration
Everphone stages and integrates all rental devices and connects them to your software stack (MDM/ITSM).
2. Compliance
Everphone rental devices are compliant with regulations such as GDPR and NIS. Private user data is separated. We also give a full audit trail and CO2 documentation.
3. Two-way handling
Everphone delivers and retrieves devices in direct contact with the end user. No more return tasks for your IT team, no more unused legacy devices in your storage.
4. Scale up or down
We centralize and automize device handling for your national teams and abroad. Scale up (or down) according to your needs and development.
Optimize your mobile ecosystem with our add-on services
One-day migration to DaaS model thanks to buy-and-rent-back (BARB) transfer
Out-of-the-box readiness for your mobile projects
To stay ahead, you need smarter, simpler solutions. The Everphone platform fully automates device management and logistics, so that your teams can focus on strategic digitization projects with real added value.
Successful enterprises use Everphone
From medium-sized businesses to global corporations, many well-known companies trust in Everphone.
Click here for our success story overview or click on the logos to learn more.
Backed by partners. Inspired by your needs.










Your road to True-DaaS
-
Submit your request
Fill in the form. -
We reach out
An expert will contact you to understand your needs. -
The Everphone offer
Get to know our solution. On demand, we’re happy to give you a tailored demo of our platform and services. -
Next steps
If it’s a fit, we’ll guide you through rollout options.