Companies today equip employees with a growing number of mobile devices. Smartphones, tablets, and laptops are integral parts of everyday work—especially in hybrid and decentralized organizations. Every new device adds additional access points to cloud services, internal applications, and third-party tools. Managing these access points quickly becomes confusing if not systematically organized.
Digital workplaces and the risk of fragmented access
Uncoordinated password practices in day-to-day operations lead to reused login credentials, insecure notes, or improvised storage locations. Combined with mobile devices used on the go, the risk of data leaks increases significantly. Security is no longer just an IT issue; it becomes a structural task for the entire organization.
Mobile devices as a security asset, not a vulnerability
Modern enterprise mobility strategies focus on managing devices centrally, enforcing policies, and providing automated security updates. Yet there remains a gap if identities and passwords are not integrated into the same security framework. A secured smartphone loses its protective effect as soon as insecure login credentials are stored or shared on it.
The challenge is to combine security with ease of use. Employees expect smooth access to the applications they need, while IT departments require control and transparency. It’s precisely at this intersection where the success of productive and secure mobile work is decided.
Passwords as part of the corporate infrastructure
Passwords are often seen as an individual problem; in reality, they are a central component of the IT infrastructure. They regulate access to systems, data, and processes. In companies with many mobile users, this creates complex dependencies: one compromised password can affect multiple services and quickly impact other areas.
That’s why a structured approach to managing login credentials is becoming increasingly important. A password manager for businesses allows for centralized management of login data, enforcement of policies, and traceable access. What matters is not just the technical implementation, but also the integration into existing device management and security processes.
Integration into mobile device management strategies
Companies that use Device-as-a-Service models benefit from standardized processes throughout the entire lifecycle of a device. From provisioning to day-to-day use, to return or recycling—security requirements can be implemented consistently. Login credentials should be integrated into this lifecycle.
When a device is reassigned or an employee leaves the company, access rights must be quickly adjusted or revoked. Isolated password management complicates this process. Integrated solutions reduce manual interventions and minimize the risk of outdated access remaining active.
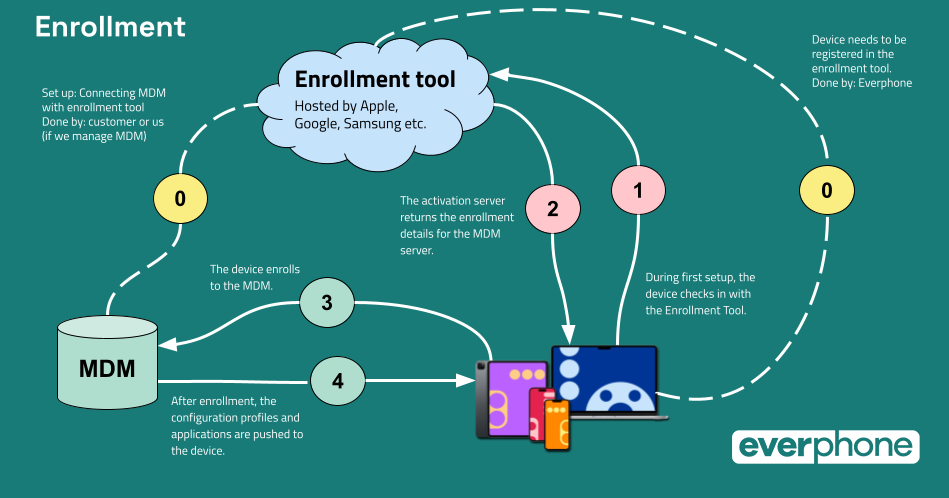
Compliance, transparency, and traceability
Regulatory requirements such as ISO standards or industry-specific regulations demand traceable security measures. This includes documenting who can access which systems and when. In mobile environments, this transparency is difficult to achieve without suitable tools.
Centrally managed login credentials create clarity. Permissions can be assigned based on roles, changes are logged, and access can be reviewed. For IT and security teams, this means less effort during audits and a stronger foundation for risk assessments.
User acceptance as a critical success factor
Technical security alone is not enough if it’s bypassed in daily work. Employees resort to insecure workarounds as soon as processes become too complex. Especially for mobile devices used under time pressure, intuitive handling is crucial.
A well-implemented password strategy reduces friction rather than increasing it. Single sign-on approaches, automatic filling of credentials, and clearly assigned responsibilities promote acceptance. Security is no longer seen as a hurdle but as a supportive part of daily work.
Outlook: Identities instead of isolated passwords
In the long term, companies are moving away from password-only models towards holistic identity concepts. Biometric methods, hardware tokens, and context-based access decisions are becoming more important. Still, passwords remain relevant in many systems—especially when integrating existing applications.
For companies, this means choosing today’s solutions to support tomorrow’s developments. A flexible architecture that integrates with modern device management and security frameworks lays the foundation for scalable and sustainable security strategies.
Interaction between IT, security, and workplace management
Managing mobile devices, access, and identities can no longer be organized in silos. Successful companies view the digital workplace as a holistic system. IT, security, and workplace management work closely together to ensure both productivity and protection.
This collaboration makes it clear: password security is not an isolated detail—it’s a central building block of modern corporate IT. Those who think strategically about mobile work will integrate login credentials into their device and security concepts right from the start.
Transparency note: This article is a guest post from a cooperation partner.