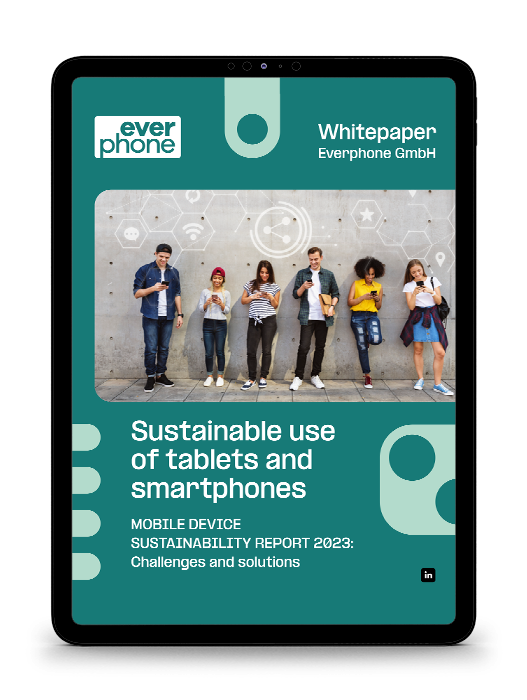
Mobile Device Management (MDM) and Mobile Application Management (MAM) are terms that people often mistakenly believe to mean the same thing. Thankfully, this popular misconception is easy to resolve. In this article we explore the differences between MDM and MAM. And we examine how both can help to improve the management of your business.
What is MAM?
Mobile Application Management (MAM) allows you to control and monitor business data in your users’ devices such as iPhones and Android phones.
With an MAM software you can set up application management policies. This is to prevent users from moving business data to unauthorized places. And you can remove data that you no longer want your users to access.
Some of the leading MAMs on the market today include Sophos Mobile, IBM Security MaaS360 with Watson, Jamf Pro, and Esper.
What is MDM?
Mobile Device Management (MDM) is a type of management or security technology. It allows IT administrators to manage and secure corporate or personal mobile devices.
MDM software allows businesses to protect your business data and fully control your fleet of mobile phones. There are various kinds of MDM software. They can function across multiple operating systems and a wide range of digital devices.

Today, such a large portion of our working lives is governed by the mobile devices we use. The portability and sophistication of smartphones is great. But it also presents some challenges for organizations that deal with sensitive communications and data. This is where MDMs can play a huge role.
Some of the leading MDMs on the market today include Flyve MDM, SOTI MDM, Hexnode, ManageEngine, Headwind MDM and Microsoft Intune.
The differences between MDM and MAM
As you can see from the definitions above, the simple difference between MDM and MAM is that MDM is about control of devices like tablets and smartphones, whereas MAM is about controlling specific corporate applications and their data.
In principle, MAM can also be dexcribed as a sub-field of MDM. Beyond this basic difference, there are further distinguished characteristics and MDM features that make MDM different from MAM.
For example:
- MDM allows you to control, monitor and manage apps by allowing you to control the actual device. On the other hand, MAM controls apps with specific features that can be modified by administrators.
- MAM allows enterprises to avoid device-level management and focus only on the elements that are relevant to the business. In fact, unlike with MDM, IT administrators would not be able to view or interact with personal data or personal apps when using MAM.
- With MDM software you can make drastic changes to your users’ devices whereas MAM is limited to apps that are relevant to your business operations.
- With MAM you have more fine-grained control and have the potential to make more nuanced changes. This often makes MAM a better fit for Bring-Your-Own-Device (BYOD) than MDM.
The similarities between MDM and MAM
Despite these basic differences there are also some similarities between MDM and MAM.
For example:
- Both MAM and MDM are usually included in EMM or UEM product suites. They are often sold together as part of a comprehensive strategy to control mobile management and security.
- Both MAM and MDM provide app wrapping and containerization features that IT administrators can use to control and update apps on managed devices.
- Both MAM and MDM contain user and group authentication and authorization. Equally, access management and access for third-party product integrations are common capabilities across both MAM and MDM.
- Both can be used to effectively manage, monitor and improve the way employees interact with the digital sphere of your business.
Using MDM and MAM to improve your business
Both MDM and MAM can be used to enhance your business process and improve your overall security. Whether you are preventing an employee from copying business data from one app to another with an MAM, or you need a MDM to securely lock and wipe a device that has been stolen, both systems can be a reassuring and effective tool to have in your bag.
If you are thinking about mobile security and management then you may also be thinking about the kinds of phones you want your employees to have. Not sure about MDM costs? Feel free to reach out to us.
Acquiring high-end smartphones is key to facilitating creativity, communication and effective business decisions. Once you’ve got the hardware you can then make final decisions about the kind of MDM and MAM software you want to use.