Mobile Threat Defense
You shouldn’t leave the protection of your mobile devices against cyber threats to chance. As a DaaS provider, we believe it is very important to offer a comprehensive service—this includes the best possible protection of devices against mobile attacks.




Mobile Threat Defense:
Why is it so complicated?
Selecting and implementing dedicated software for mobile threat defense is not easy. The fundamental challenge is to find a secure MTD solution at a reasonable cost—and to integrate it into the software landscape with predictable effort. However, there are factors that delay or even prevent the implementation of MTD projects.
Timing
Time is pressing, but IT security projects are complex and lengthy. Diversified solutions generate long-term expenses.
Costs
Security solutions and service providers are expensive, in particular the administration of several parallel security tools.
Alignment
The decision to use a security tool has far-reaching consequences and must be coordinated with stakeholders.
Configuration
The time and effort required for configuration is often underestimated. Managing tools and/or providers is labor-intensive.
Know-how
Staff training to build internal knowledge and hire competent IT resources costs time and money.
Operation
Not only do configuration and deep integration require effort, but so does ongoing operation. This is often forgotten.

More than just security software:
Mobile Threat Defense
At Everphone, we see Mobile Threat Defense as more than just security software. Our aim is to bundle all services related to mobile devices in companies. The goal: high cost efficiency and reduced workload with maximum data security.
Comprehensive protection on all attack vectors
We want to protect your data across the entire attack surface: apps, OS, files, networks. In addition to licensing an MTD tenant, we provide support for policy definitions, SIEM integration, and tenant setup.
Easy deployment, even for large device fleets
Our service ensures that entire fleets of devices are secured at the push of a button. Even if there are thousands of devices involved: the MTD solution is deployed across the entire fleet within minutes.
User-friendly and data protection compliant
Mobile threat defense software must not impair the performance (and thus the user-friendliness) of the devices. At the same time, data protection requirements (DSGVO, NIS-2 etc.) and works council requirements must be met.
Cloud-based sandboxing with Check Point
Licensing a security solution is a cornerstone of our security package. Together with our partner Check Point, we provide “Harmony Mobile” licenses and support you with deployment. We do this for devices that you rent from us as part of the DaaS package—and for your other mobile devices as well.
We help you with tenant creation, tenant management, remote lock and wipe, and provide you with user and admin support.
Case study: Mobile Threat Defense in critical infrastructure environments
As a supplier of electricity, gas, water and district heating, the municipal utility company Stadtwerke Dinslaken is part of the critical infrastructure (KRITIS) in Germany.
In the video, Benjamin Wiehn, who, as head of IT, is responsible for securing the IT infrastructure, explains how a mobile threat defense solution was rolled out to the 400 cell phones of the municipal utility company using Everphone.
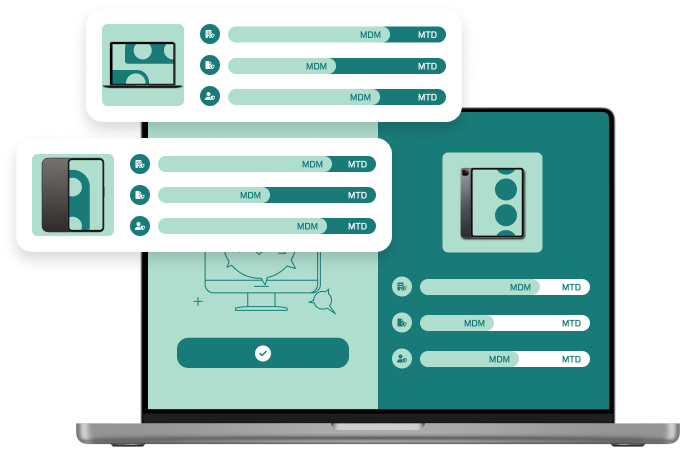
An MDM is not enough!
More than 90 percent of all companies already use mobile device management software. This helps to close some security gaps (e.g. outdated operating systems, as the MDM can be used to force patches and OS updates on the devices).
However, MDM is completely powerless against many other mobile threats. Only when MDM and MTD solutions work together can the company device be secured against malware, phishing, bots, etc. You can find more information in the security white paper.
Mobile threats
Attack vectors on mobile devices
Their widespread use makes smartphones and tablets a favorite target of cybercriminals. Because an MDM does not protect against these threats, a dedicated MTD solution is essential. There are many potential points of attack.
Whitepaper: mobile security
Our white paper summarizes all the relevant information on mobile security for you.
It is free to download.
Table of contents:
- Background
- Legal requirements
- Threat landscape
- Security strategies and measures
- Outlook
Start with Mobile Threat Defense now
Talk to our security experts
Our MTD team will be happy to help you with advice and assistance.
Leave your contact details here and we will get back to you. With no obligation.