Five years ago, the trend seemed unstoppable: using your own laptops, MacBooks and smartphones on the job was the thing. The numbers for BYOD continue to rise steadily – but the enthusiasm has since suffered a few dents. We ask: Is “Bring Your Own Device” still viable for the future?
 Working on a private device: „Bring Your Own Device“ is still a thing in many companies
Working on a private device: „Bring Your Own Device“ is still a thing in many companies
Background: BYOD and consumerization
First of all: In the following, I always write about BYOD in the corporate context. The use of the same name in education (i.e. BYOD in schools and universities) is not something completely different, but is not meant explicitly. So back to the companies.
It all sounded so good!
The C-level was impressed, the HR department was happy. Employees simply bring their own devices to the workplace. How simple, how ingenious: you know your way around with them, you can be productive with them right away. And think it’s cool too.
Do-it-yourself mobility, ad hoc digitization, consumerization, smart working, home office , remote and cloud and whatever else was included in the “Bring Your Own Device” word salad.
And the best thing about it: the employer saves the costs of purchasing the devices the employees have already brought with them.
 IT, procurement and finances are eager to jump on the BYOD train to save time and money
IT, procurement and finances are eager to jump on the BYOD train to save time and money
What sounds like a pure win-win situation is, on closer inspection, not quite as advantageous in many companies: The question of costs actually only raises further questions, because the savings are offset by high IT costs. All the devices you bring with you have to be securely integrated into the company’s networks – that ‘s where mobile security becomes a Sisyphus task and “monkey work”.
Click on the button to load the content from giphy.com.
There are also legal pitfalls. Lawyers warn of data protection controls and dissuations in connection privacy regulations such as the European GDPR. Employers and employees are equally unsure: Can I still use WhatsApp now? Or FaceTime? There are many uncertainties and dangerous half-knowledge here.
So is the BYOD concept still viable?
I don’t think so. There are better alternatives. Let’s go through the matter.
Greater productivity with Bring Your Own Device (BYOD)
The background to many BYOD scenarios is often the fact that employees privately own the better hardware. This is actually quite sad. Understandably, if workers have a fast MacBook at home, they don’t want to sit down with some antique dual-core Pentium bucket to work in snail’s pace and wait five minutes on a browser tab to open.
The same applies to smartphones and tablets: if employees – regardless of whether they are from Generation X, Y or Z – are offered an entry level Android phone from China as a company cell phone, they are sure to pull a long face. Employee satisfaction won’t be increased that way.
BYOD, employer branding and employee motivation
A company cell phone “downgrade” is definitely not a positive user experience. In the worst case, it not only does damage the individual employee motivation, but the entire employer profile.
If, for example, facts about the technical equipment are happily shared in employer rating portals, often garnished with cynical remarks by disappointed employees. Is it not better than to boost the BYOD strategy after all?
Millennials want mobile work
In recent times, employee demands on the workplace have shifted. Millennials expect technical equipment that allows them to be productive; that doesn’t slow them down. Remote work and working on the go are a natural part of this. Since the smartphone is the most important privately used technical device today, this expectation naturally extends to mobile devices.
Anything, anytime, anywhere
“Always on”? No, thanks.
Millenials don’t want to be available for work 24/7. And they also don’t want to carry two smartphones around with them.
But they do want to be able to complete tasks from anywhere at any time – “anything, anytime, anywhere”. However, if there’s no suitable mobile device provided, this expectation stays.
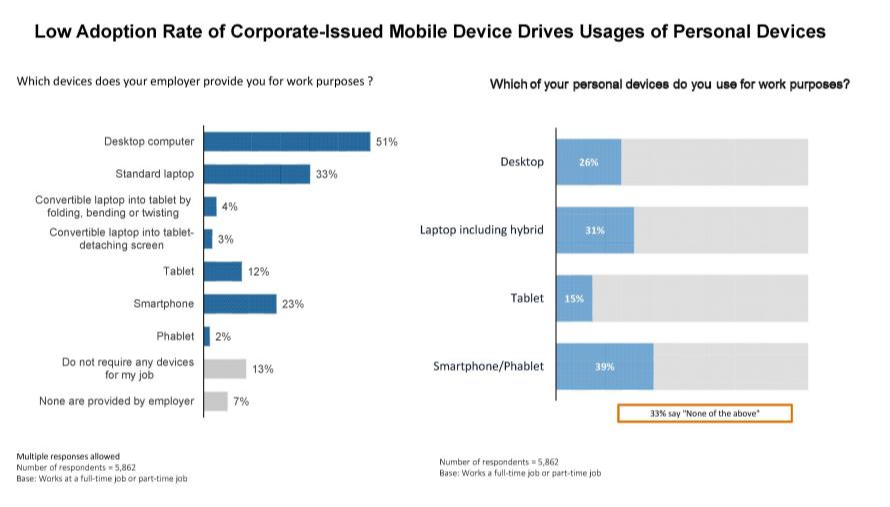
Result: Employees use their private smartphones for both private and business purposes (“dual use”). Even if there is no transparent regulation in the company or even if this use is explicitly not allowed. As Evernote, Slack, Dropbox, Asana, Trello, Wunderlist and other productivity apps are so useful, they are going to be used anyway.
And this is where the real problems start – this can threaten the IT security of the entire company and have far-reaching consequences under employment law.
Software Licenses and Copyright
The first of the legal issues related to BYOD concerns the licensing of programs installed on the mobile device. Not every privately purchased software is also intended for commercial/entrepreneurial use. Through this “extended” use, employees may infringe copyrights.
Liability in the event of damage or loss of the end device
What happens if the employee loses the device during professional use, for example in the field or at a trade fair? Or if the device is damaged during work or does not function efficiently? Who is liable then?
In principle, the following applies: If a private device is used with the knowledge and interest of the company, damage to or loss of the device during normal working hours is attributable to the employer.
In case of doubt, it is of course difficult to prove that the device fell down while reading an email for the job. A controversy then seems quite probable.
Mobile security: Liability in the event of a security breach
If, on the other hand, the damage occurs on the company side due to a breach of security regulations, the employee can also be held liable. It is therefore advisable to specify in a user agreement the extent to which the employee has a duty to cooperate in mobile security and securing the IT infrastructure.
This can mean, for example, that the employee must regularly update apps and/or the operating system or that they aren’t allowed to root/jailbreak their smartphone. In addition, employees in BYOD scenarios need to be made aware of app security: Not every app from the App Store or Google Play is harmless. In the worst case, passwords are tapped or malware is installed, which can lead to data theft, industrial espionage and blackmail (“ransomware”).
Data protection, privacy acts and Bring Your Own Device
BYOD scenarios require strict separation of private and business data. Otherwise, there is a risk of violations of personal rights, for example, if the company includes private data on the end device as part of remote monitoring.
In this case, employers may even be liable for damages, as the employee’s right to informational self-determination is violated.
Another problem is the storage of personal data from the company on private devices. If employees use the messenger service WhatsApp in an EU country, for example, they are in violation of the GDPR privacy regulation.
This is because the app sends contact data to servers outside the European Union without the consent of those affected. This could result in heavy fines in the event of a data protection audit.
Data protection: solutions for BYOD
There are technical solutions for the correct use of BYOD under data protection law.
Data protection with container app
One variant is mobile application management with the help of a container app. A container is an encrypted area on the smartphone.
Company data and contacts are stored separately in this segregated area. IT can use a pre-configuration to prevent the installation of unwanted applications in the container (“blacklisting”) and the copying of data files to the private area. If the device is lost, the company data from this area can also be remotely deleted (“wiping”) and the device locked (“locking”). Disadvantage: There are costs for the license and IT effort.
Known container apps are, for example, Knox from Samsung, the VMware AirWatch container or SecurePIM.
Data protection through mobile device management (MDM)
Mobile device management software is another option. MDM programs usually also include a module for containerizing apps, but also offer other functions.
{{cta(‘ab25542c-49ed-4a8b-b99d-bf6d6f0575de’)}}
 The GDPR rules that personal and business data have to be divided on end devices.
The GDPR rules that personal and business data have to be divided on end devices.
Otherwise companies risk fines of up to 20,000,000 Euros or 4% of their annual revenue
BYOD and IT security
In addition to data protection problems, BYOD also raises security risks. Statistics show that almost every fourth mobile device is stolen or lost. A stolen company cell phone can be the key to valuable company data for a hacker – and is therefore the nightmare of every IT manager.
Bring Your Own Security Risk
A major source of danger is when unauthorized persons gain access to the device. This does not necessarily have to be done by stealing the hardware. Malicious software (viruses, trojans, etc.) can also open gateways and result in data deletion or data theft.
Since the devices brought along – depending on the size of the company – usually run on many different Android and iOS versions, the secure integration of the mobile devices into the network structure of a company is a real challenge for IT. In most cases, the active participation of the employees is also required here, keyword: raising awareness.
The apps on smartphones and tablets often access cloud apps, such as the Dropbox storage service. It’s also practical when data is synchronized on the mobile device, the work laptop and the desktop PC at home. However, such services can also cause data leaks if, for example, insecure passwords are used.
Whether BYOD devices are more of a curse or a blessing for the company can be answered quite clearly from a security perspective. Lenovo states in their Think Progress blog: “A company’s data is only ever as secure as the most insecure device.”
BYOD – advantages and disadvantages in conclusion
Let’s recap briefly.
Bring Your Own Device Benefits
- Cost savings for the company when purchasing mobile devices
- BYOD devices tend to be more powerful
- increases employee productivity
- increases employee satisfaction
- facilitates remote work, home office, mobile work
BYOD – Disadvantages
- high IT expenses due to heterogeneous software and hardware line-up
- IT security aspects (data leaks, malware, security breaches)
- Data security (industrial espionage, hackers, data loss
- Data protection problems (GDPR, separation of professional and private data, remote monitoring and much more)
- The legal situation for use is unclear if there is no express user agreement
- Copyright violations due to missing software licenses necessary
- Usability/acceptance low if, for example, the private device has to be left to the IT administrator
- Danger of data silos
- in the worst case, loss of control over the company’s client landscape
Incidentally, you can find a comprehensive analysis of the risk factors in our blog article on BYOD risks.
Is there no alternative to BYOD?
There is.
With “Choose Your Own Device” companies have the opportunity to use company mobile phones with legal certainty and with little IT effort and still save on acquisition costs. The basis for this is a company mobile phone rental model. In addition to the advantages of GDPR compliance, mobile device management and a quick replacement service in the event of a defect, companies can also use the company device as an employer benefit.