BYOD (bring your own device) is a reality in many organizations. Using the mobile devices of employees can save companies a lot of money and are a shortcut for these lengthy procurement processes. However, BYOD can become a major security risk.
What is BYOD? What is MDM?
BYOD simply means that employees use their personal mobile devices also for work. This may seem logical: they already own these devices (thus they don’t need to be bought) and are familiar with them, which increases productivity.
However, they can be a major risk for the organization. Nobody knows if given employees might obtain apps from insecure sources such as internet forums or if they regularly update their mobile operating systems. And there’s still the problem of many apps sharing data in a way which is not compliant with privacy regulations. A well-known example is WhatsApp. Its communication with servers in the USA is a clear breach of the EU’s data privacy regulation, the GDRP.
BYOD and containerization
The company data needs to be safe. It is therefore necessary to separate it from the personal data on the phone and detach it from given personal apps. This “containerization” can be obtained in two ways: by installing a so-called container-app or by installing MDM software.

MDM software unifies all company devices. It means that company phones, tablets, and more, can be managed, controlled, and updated from a central hub by the business IT Management team. When devices such as smartphones and tablets are company-issued, the process is simple, as the software already exists on the devices before they are given to employees. In the case of Bring-Your-Own-Devices, the software is added afterwards.
Why should employees use their own devices ?
There are several reasons that an employee might prefer to use their own device, rather than accepting a company-issued phone:
- They can choose the device and operating system that suits them
- They will only need one device at any given time, rather than having a personal phone and a work phone
- There is no confusion about whether they can use their phone for private calls, texts, and data, as the device is theirs, not the company’s
- They may see this as an opportunity to invest in a better device, as part of the monthly cost will be reimbursed
While all these points are valid, they leave out one very important aspect: employer branding. Many employees don’t think at all that it’s “cool” to have to bring their own device. To the contrary, many expect to be handed a company phone as part of their workplace equipment. And this is exactly what companies should do: Offer them the phone of their choice. We call this approach “choose your own device” (CYOD).
Click here to learn more about CYOD.
Why should an employer invest in BYOD and MDM?
For an employer, the decision is not an easy one. Devices chosen by the employees that are not owned and distributed by the company come with significantly higher privacy risks, as we shall explore further. But there are still notable benefits to BYOD MDM for employers:
- Your MDM budget stretches further than with COPE devices (Corporate-owned, privately-enabled), as employers only cover part of the monthly costs
- Employees are likely to be more productive with familiar devices
- Employees are responsible for device sourcing, maintenance, and often repairs
Issuing company devices without MDM software
Without MDM software, managing devices used for work purposes would be impossible. In the industry, we call this Dark BYOD; when companies have little to no control of unauthorised devices.
In this instance, employers would have to rely on employees to run updates and download company software onto their phones. Monitoring productivity, and keeping all staff up-to-date on tasks and workflows would have to be done by direct communications and word-of-mouth, rather than the apps and shared information portals made possible by MDM. With MDM, employers can keep track of device usage with far more efficiency.
MDM software reduces the pressure on the company’s IT department. It reduces time spent helping individuals with specific problems on unique devices and facilitates network-wide patches whenever errors occur.
The biggest risk with Dark BYOD, however, is security. Every device is vulnerable, whether it is owned by individual employees, by the company, or a mix of both. With no MDM supervision, however, businesses may remain blissfully unaware when a data breach or malware attack has occurred, finding out only when it is too late.
BYOD and privacy risks
With Bring-Your-Own-Devices, there are risks for both the employer and the employee, even when MDM software has been installed. Understanding the risks will help you mitigate them, and put plans in place for dealing with data breaches.
When an employee agrees to have company software installed on their phone, they open themselves up to their own set of privacy risks. Employers are able to access a device that contains a lot of private data, as well as a wealth of personal memories, photographs, and communications. It is essential, therefore, that the company understands GDPR regulations thoroughly and takes every step to protect its employees.
For the company itself, there are many privacy risks that must be accounted for. That is the case because security on BYOD devices is limited.
- Employees are responsible for endpoint security on their devices. Even with security apps installed via MDM software, they may still be vulnerable to phishing attacks or insecure network connections.
- Data can be transferred off company phones onto external devices, such as USB sticks and personal laptops.
- Malware can be introduced into the company network from infected devices when employees connect in the office.
- Licence violations, such as End User Agreements violations, can occur when employees use paid-for apps for personal means.
- Popular communication and messaging apps transmit chat history data to international servers, which violates company data protection regulations.
BYOD and data separation
GDPR is strict about companies processing or accessing personal data unnecessarily. For this reason, it needs to be made clear to the employee what data will be accessible to the company and what company data must not be downloaded onto the device. Equally, the company has a responsibility not to overstep when monitoring devices via the MDM software.
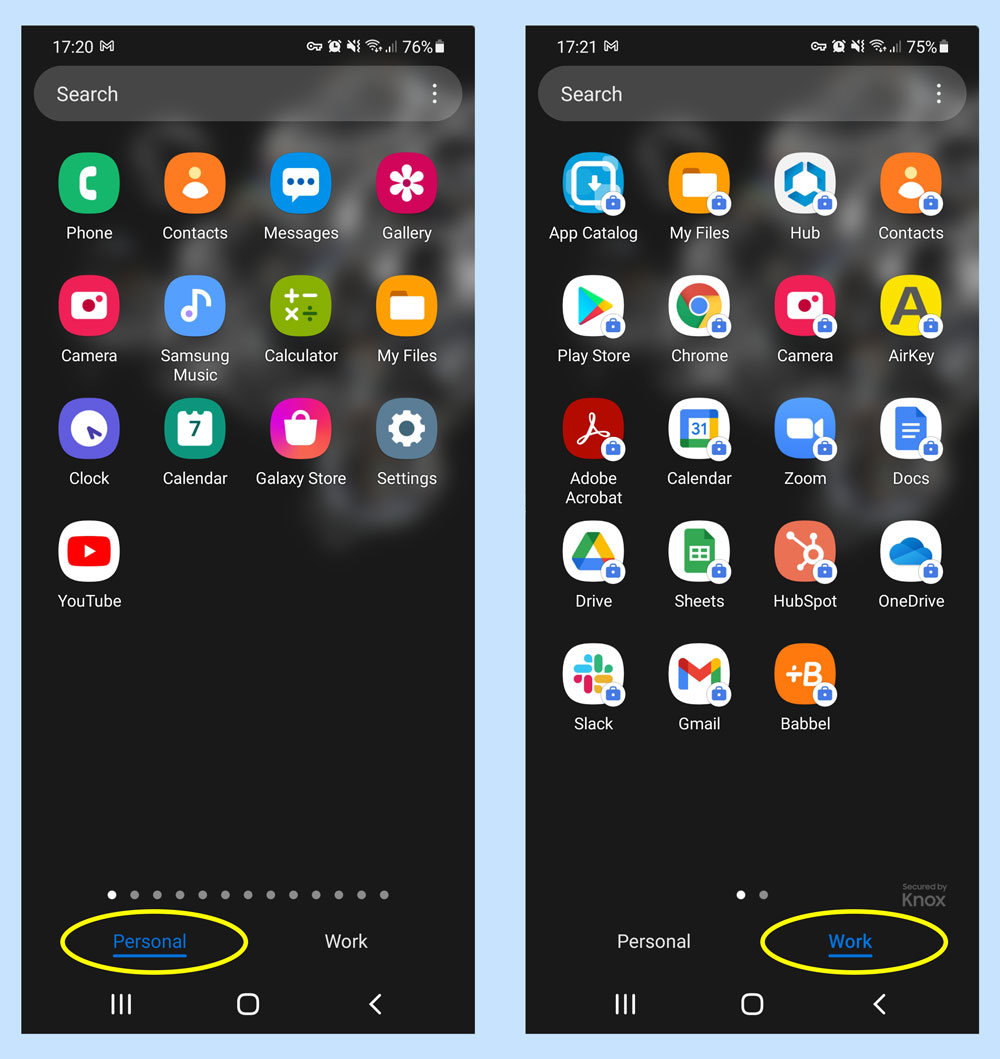
Encrypted container as used on an Samsung Galaxy Android Phone (right)
There are, however, means by which businesses can restrict access to corporate data on employee devices. Employers can restrict which apps are able to open specific files, which mail apps can open and send business emails, and what documents can be opened within business-owned apps on the device. These features are dependent on the type of device you choose (Apple, Android, Microsoft ettc.) and which MDM software you choose. Read on to find out more about the data separation features available with Apple or Android devices.
From BYOD to CYOD: Let the employees decide
The main benefit of the BYOD strategy is, that your employees use a device they already know. But maybe they would prefer a different one? Maybe they only use the iPhone “mini”, because the “Pro Max” was too expensive?
With “CYOD”, you can offer them a variety of smartphones to choose from. Whether you set restrictions on the type of hardware they can select is something to be decided by you. But why would you? Both iOS and Android devices can be integrated safely into the companies network with almost any MDM software.
MDM with Apple devices
One key feature of using iOS devices is the built-in container solution that helps to keep business and personal data separate within the same device. This extends to apps, VPN, notes, keychain passwords, iCloud accounts, Mail apps, and calendars. Everything connected to the business is labelled as ‘managed,’ while personal apps, data, and files are labelled as ‘unmanaged.’ In the case of an employee’s termination, all ‘managed’ apps and data can be removed via the central MDM software.
MDM with Android devices
If you prefer Android devices, MDM solutions for Android offer something called the Work Profile, which separates all personal phone use from company use. And it can be controlled from the MDM dashboard. The Work Profile works in a similar way to Apple devices, as explained above, with everything outside the profile being kept entirely separate. Personal apps cannot influence anything within the Work Profile. And the Work Profile can be deleted without authorisation from the device owner.
Whether you choose iOS, Android, or something else for your BYOD network, be clear on your company policy for device usage. Putting together an effective, watertight, and future-proof User Agreement Contract will help bring clarity for your employees. And it will keep company data safe.
Establish a clear MDM user agreement contract
In the case of using BYOD MDM, a clear, binding, technical framework must be established and agreed to by both the company and the employees who will be using the device.
This framework must take into account the GDPR responsibilities of the company, as well as the security responsibilities of the individual.
User agreements of this kind are often viewed by employees as an infringement of their rights, or a restriction of their liberty when it comes to using a device that is technically their own. For this reason, establishing a strict but viable list of ‘dos and don’ts’ is essential for the contract to work. It is also essential for the employee to feel confident using their BYOD phone.
Where possible, outline responsibilities and who they fall to. While the employer might be responsible for the device, due to the BYOD contract the employee may be held accountable if avoidable privacy breaches (such as dangerous file- or app-downloads) lead to company damage.
Device-as-a-Service: A secure alternative to BYOD MDM
BYOD MDM may be the best solution for small businesses, thanks to the cost-saving possibilities. But for larger businesses, a far more viable option is the Device-as-a-Service model offered by Everphone. Rather than purchasing company devices outright, or asking your employees to source their own devices, you can rent the newest hardware from us and make use of the best MDM software. We handle distribution, faulty device replacement, and give you a proven MDM system that will minimise the risks to both you and your employees.
Device-as-a-Service is a solution to the privacy concerns of BYOD and gives your employees the freedom to use their work phones for private use. It also ensures that every one of your team members has access to the exact devices they need. Whenever they need them.