Vor fünf Jahren schien der Trend noch unaufhaltsam: eigene Laptops, MacBooks und Smartphones im Job einzusetzen, war das Ding. Die Zahlen für BYOD steigen weiterhin ständig – die Begeisterung hat mittlerweile aber einige Dellen bekommen. Wir fragen: Ist „Bring Your Own Device“ noch zukunftsfähig?

Mit dem Privatgerät arbeiten: „Bring Your Own Device“ ist nach wie vor beliebt
Hintergrund: BYOD und Consumerization
Eins vorweg: Ich schreibe nachfolgend von BYOD immer im Unternehmenskontext. Der gleichnamige Einsatz im Bildungswesen (also BYOD in Schulen und Universitäten) hat hierzu zwar Berührungspunkte, ist aber nicht explizit gemeint. Also zurück zu den Firmen.
Es klang alles so schön!
Das C-Level war angetan, die HR-Abteilung happy. Mitarbeiter*innen bringen einfach ihre eigenen Endgeräte mit an den Arbeitsplatz. Wie einfach, wie genial: Mit denen kennen sie sich aus, mit denen können sie gleich produktiv sein. Und finden es auch noch cool. Mobility zum Selbermachen, gelebte Digitalisierung, Consumerization, Smart Working, Home Office, Remote und Cloud und was nicht alles in der Wortwolke „Bring your own Device“ noch so mitklang.
Und das Beste daran: Der Arbeitgeber spart sich auch noch die Kosten für die Anschaffung der mitgebrachten Geräte.
 Einkauf, Finances und Geschäftsführung wittern mit BYOD kräftige Einsparungen
Einkauf, Finances und Geschäftsführung wittern mit BYOD kräftige Einsparungen
Was klingt wie eine reine Win-win-Situation, ist bei genauerem Hinsehen allerdings in vielen Unternehmen doch nicht ganz so vorteilhaft: So wirft die Frage nach den Kosten eigentlich nur weitere Fragen auf, denn den Einsparungen stehen hohe Aufwände in der IT gegenüber.
Die ganzen mitgebrachten Geräte müssen ja sicher in die Netzwerke des Unternehmens integriert werden – da wird Mobile Security zur Sisyphos-Aufgabe und zur „Monkey Work“.
Im Akkord BYOD-Smartphones ins Netzwerk einzubinden und zu konfigurieren macht nicht jedermann Spaß
Zudem drohen rechtliche Fallstricke. Rechtsanwälte warnen im Zusammenhang von Firmenhandys und DSGVO vor Datenschutzkontrollen und Abmahnungen. Arbeitgeber und Arbeitnehmer*innen sind gleichermaßen verunsichert: Darf ich jetzt noch WhatsApp nutzen? Oder FaceTime? Hier gibt es viele Unsicherheiten und gefährliches Halbwissen.
Ist das Konzept BYOD also noch tragfähig?
Ich meine: nein. Es gibt bessere Alternativen. Aber alles der Reihe nach.
Mehr Produktivität mit „Bring Your Own Device“ (BYOD)
Hintergrund vieler BYOD-Szenarien ist oft die Tatsache, dass Mitarbeiter privat über bessere Hardware verfügen, als das Unternehmen, in welchem sie angestellt sind. Traurig eigentlich, aber klar: Wenn ich zuhause im Besitz eines flotten MacBooks bin, habe ich keine Lust, mich im Job an irgendeine Uralt-Dual-Core-Pentium-Möhre zu setzen, die fünf Minuten braucht, um einen Browser-Tab zu öffnen.

BYOD: Nicht alle Unternehmen bieten ihren Mitarbeiter*innen die aktuellen Flaggschiff-Modelle von Apple oder Samsung an. Gegebenenfalls nutzen Angestellte dann lieber ihre eigene Hardware
Das gleiche gilt für Smartphones und Tablets: Wenn Angestellte – und zwar egal, ob aus der Generation X, der Generation Golf oder der Generation Y – als Firmenhandy ein chinesisches Billiggerät überreicht bekommen, gibt es lange Gesichter anstelle erhöhter Mitarbeiterzufriedenheit.
BYOD, Employer Branding und Mitarbeitermotivation
Ein Firmenhandy-„Downgrade“ ist definitiv kein positives Nutzererlebnis. Im schlimmsten Fall schädigt es nicht nur die individuelle Mitarbeitermotivation, sondern das gesamte Arbeitgeberprofil – wenn etwa Fakten zur technischen Ausstattung in Arbeitgeber-Bewertungsportalen genüsslich und mit zynischen Bemerkungen breitgetreten werden, garniert von enttäuschten Employees oder ausgeschiedenen Angestellten.
Millenials wollen Mobiles Arbeiten
Generationsbedingt haben sich die arbeitnehmerseitigen Ansprüche an den Arbeitsplatz verschoben. Besonders mit der Covid-Pandemie.
Millenials erwarten eine technische Ausstattung, mit der sie produktiv sein können und die sie nicht auch noch ausbremst.
Remote-Arbeit und Arbeiten von unterwegs gehören hier selbstverständlich mit dazu. Da das Smartphone heutzutage das wichtigste privat genutzte technische Gerät ist, erweitert sich dieser Anspruch wie selbstverständlich auf die mobilen Endgeräte.
Anything, anytime, anywhere
„Always on“? Bitte nicht.
Millenials wollen nicht 24 Stunden am Tag für die Arbeit erreichbar sein.
Und sie haben in der Regel keine Lust, zwei Smartphones mit sich herumzutragen.
Aber: Sie wollen Tasks jederzeit von jedem Ort erledigen können – „anything, anytime, anywhere“. Nun klafft zwischen diesem Anspruch und der Realität insofern eine Lücke, als die Ausstattung mit geeigneten Mobilgeräten durch die Arbeitgeber zu niedrig ist.
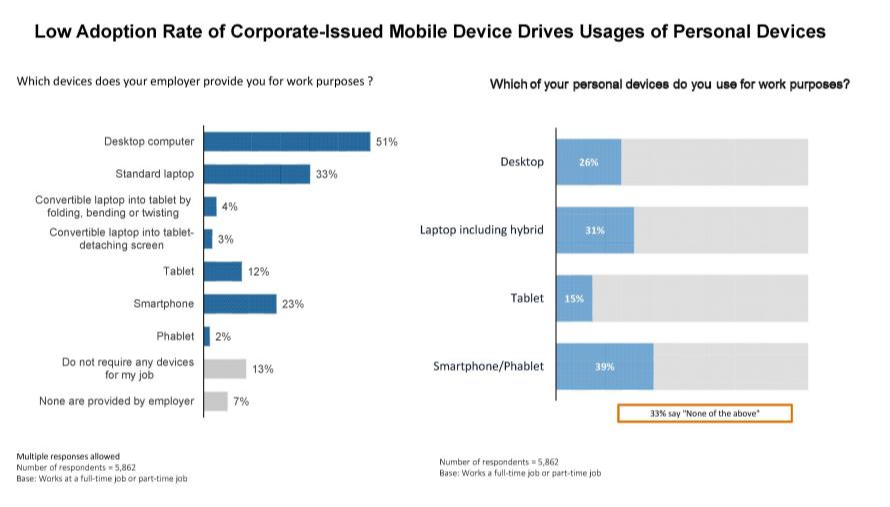
Zwischen beruflich genutzten und bereitgestellten Mobilgeräten gibt es laut Gartner-Studie eine klaffende Lücke
(Bild: Gartner)
Resultat: Angestellte nutzen ihre privaten Smartphones sowohl privat als auch geschäftlich („Dual-Use“). Selbst wenn es keine transparente Regelung im Unternehmen gibt oder sogar, wenn diese Nutzung ausdrücklich nicht gestattet ist.
Aber weil Evernote, Slack, Dropbox, Asana, Trello, Wunderlist und wie die Produktivitäts-Apps nicht alle heißen eben so nützlich sind, werden sie halt trotzdem verwendet.
Und spätestens hier gehen echte Probleme los – das kann nämlich die IT-Sicherheit des gesamten Unternehmens bedrohen und weitreichende arbeitsrechtliche Konsequenzen haben.
Softwarelizenzen und Urheberrecht
Das erste der rechtlichen Probleme im Zusammenhang mit BYOD betrifft die Lizenzierung von Programmen, die auf dem Mobile Device installiert sind.
Nicht jede privat erworbene Software ist auch für den gewerblichen/unternehmerischen Einsatz gedacht. Durch diese „erweiterte“ Nutzung verletzen Mitarbeiter*innen unter Umständen also das Urheberrecht.
Haftung bei Beschädigung oder Verlust des Endgeräts
Was passiert, wenn jemand das Gerät im beruflichen Einsatz verliert, beispielsweise im Außendienst oder auf einer Messe? Oder wenn das Gerät während der Arbeit beschädigt wird oder den Geist aufgibt? Wer haftet dann?
 Wer haftet, wenn ein mitgebrachtes Mobile Device beschädigt wird?
Wer haftet, wenn ein mitgebrachtes Mobile Device beschädigt wird?
Prinzipiell gilt: Wenn die Nutzung eines Privatgeräts in Kenntnis und Interesse des Unternehmens erfolgt, ist sie betrieblich veranlasst.
Das heißt, dass Beschädigung oder Verlust des Geräts während der üblichen Arbeitszeit dem Arbeitgeber zuzurechnen ist.
Im Zweifel ist es natürlich schwierig nachzuweisen, dass das Gerät ausgerechnet beim Lesen einer beruflichen Mail heruntergefallen ist. Hier droht also schon Ungemach.
Mobile Security: Haftung bei einem Security-Breach
Entsteht der Schaden hingegen auf Unternehmensseite durch die Verletzung von Sicherheitsvorschriften, kann auch ein*e Arbeitnehmer*in haftbar gemacht werden.
Es empfiehlt sich deswegen, in einer Nutzungsvereinbarung festzuhalten, inwiefern Arbeitnehmer*innen eine Mitwirkungspflicht bei der Mobile Security und der Sicherung der IT-Infrastruktur haben.
Dies kann zum Beispiel bedeuten, dass sie regelmäßig Updates von Apps und/oder Betriebssystem durchführen müssen oder nicht befugt sind, das Smartphone zu rooten/zu jailbreaken. Zudem müssen Mitarbeiter*innen in BYOD-Szenarien für die Sicherheit von Apps besonders sensibilisiert werden: Nicht jede App aus dem App Store oder Google Play ist harmlos.
Im schlimmsten Fall werden Passwörter abgegriffen oder Malware installiert, die zu Datendiebstahl, Wirtschaftsspionage und Erpressung („Ransomware“) führen können.
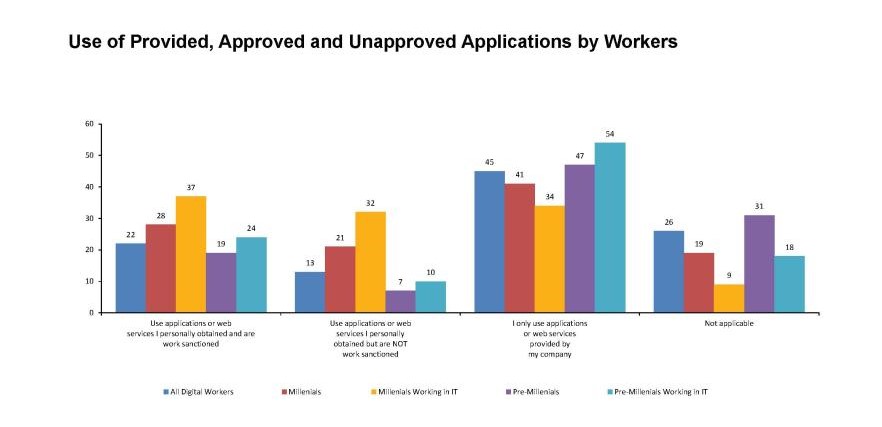 Der Anteil der Mitarbeiter*innen, die nicht genehmigte Apps installieren, liegt laut Gartner-Studie bei bis zu 32 Prozent (Grafik: Gartner)
Der Anteil der Mitarbeiter*innen, die nicht genehmigte Apps installieren, liegt laut Gartner-Studie bei bis zu 32 Prozent (Grafik: Gartner)
Geldwerte Vorteile, Zuschüsse, Steuern, Betriebsausgaben durch BYOD?
Erhalten Angestellte vom Unternehmen einen Zuschuss für den Kauf eines BYOD-Smartphones oder Tablets, ist diese Zuwendung lohnsteuer- und sozialversicherungspflichtig. Anders kann dies in einem alternativen Vergabemodell aussehen.
Wichtig ist für die steuerliche Beurteilung, in BYOD-Szenarien alle Aufwendungen zweckgebunden – also streng getrennt nach betrieblicher und privater Veranlassung – aufzuschlüsseln. Ist dies geschehen, kann der Arbeitgeber die für die betriebliche Nutzung entstandenen Kosten als Betriebsausgaben absetzen. Ihr könnt uns gerne zu den Voraussetzungen für die steuerlichen Vorteile ansprechen.
Datenschutz, DSGVO und Bring Your Own Device
Bring-your-own-Device-Szenarien setzen eine strikte Trennung von privaten und geschäftlichen Daten voraus. Ansonsten drohen Verletzungen des Persönlichkeitsrechts, zum Beispiel, wenn das Unternehmen auf dem Endgerät private Daten im Rahmen einer Fernüberwachung miteinschließt.
Hier machen sich Arbeitgeber sogar schadensersatzpflichtig, da das Recht des Arbeitnehmers auf informationelle Selbstbestimmung verletzt wird. Mehr Infos dazu sowie die BYOD-relevanten Paragraphen kannst du hier finden.
Ein weiteres Problem ist das Vorhalten personenbezogener Daten aus dem Unternehmensbereich auf den Privatgeräten. Nutzen Mitarbeiter*innen beispielsweise den Messenger-Dienst WhatsApp, verstoßen sie gegebenenfalls gegen die EU-DSGVO: Denn die App sendet ohne Zustimmung der Betroffenen Kontaktdaten auf Server außerhalb der Europäischen Union. Damit drohen bei einer Datenschutzkontrolle hohe Bußgelder.
Datenschutz: Lösungen für BYOD
Es gibt technische Lösungen für den datenschutzrechtlich korrekten Einsatz von BYOD.
Datenschutz mit Container-App
Eine Variante ist Mobile Application Management mithilfe Spezieller Apps, die einen verschlüsselten Workspace auf dem Gerät einrichten (früher sprach man von „Container-Apps“).
In diesem abgetrennten Bereich werden die Firmendaten und -kontakte separat gespeichert. Die IT kann durch einen Vorkonfiguration die Installation unerwünschter Anwendungen im Container („Blacklisting“) sowie das Kopieren von Datenbeständen in den privaten Bereich unterbinden.
Wird das Gerät verloren, können die Unternehmensdaten aus diesem Bereich auch aus der Ferne gelöscht („Wiping“) und das Gerät gesperrt („Locking“) werden. Nachteil: Es entstehen Kosten für die Lizenz und IT-Aufwand.
Datenschutz durch Mobile Device Management (MDM)
Eine weitere Möglichkeit sind Mobile-Device-Management-Softwares. Diese Programme beinhalten in der Regel auch ein Modul zur Containerisierung von Apps, bieten darüber hinaus aber auch noch weitere Funktionen. Näheres erfährst du in unserem MDM-Whitepaper.
BYOD und IT-Sicherheit
BYOD wirft neben Datenschutzproblemen aber auch Sicherheitsrisiken auf. Ein entwendetes Firmenhandy kann für einen Hacker der Schlüssel zu wertvollen Unternehmensdaten sein – und ist damit der Alptraum aller IT-Verantwortlichen.
Sicherheitsrisiko „Bring Your Own Device“
Eine wesentliche Gefahrenquelle ist, wenn Unbefugte Zugriff auf das Gerät erhalten. Dieser muss nicht zwangsläufig über den Diebstahl der Hardware erfolgen. Auch Schadsoftware (Viren, Trojaner etc.) kann Einfallstore öffnen und Datenlöschung oder Datenklau zur Folge haben.
Da die mitgebrachten Geräte – je nach Größe des Unternehmens – meist auf vielen unterschiedlichen Android- und iOS-Versionen laufen, ist die sichere Einbindung der mobilen Geräte in die Netzwerkstruktur eines Unternehmens eine echte Herausforderung für die IT. Meist ist hier auch das aktive Mitwirken der Mitarbeiter*innen gefragt, Stichwort: Sensibilisierung.
Die Apps auf Smartphones und Tablets greifen oft auf Cloud-Umgebungen, wie zum Beispiel der Speicherdienst Dropbox. Ist ja auch praktisch, wenn Daten auf dem Mobilgerät, dem Arbeitslaptop und dem Desktop-PC zuhause synchronisiert werden. Allerdings können solche Dienste auch Datenlecks verursachen, wenn etwa unsichere Passwörter verwendet werden.
Ob für das Unternehmen BYOD-Geräte eher Fluch oder Segen sind, ist aus der Sicherheitsperspektive recht eindeutig zu beantworten. Im Think-Progress-Blog von Lenovo schrieb deshalb einst:
Die Daten eines Unternehmens sind immer nur so sicher wie das unsicherste Gerät.“
BYOD – Vorteile und Nachteile im Fazit
Fassen wir noch einmal kurz zusammen.
Bring-your-own-Device – Vorteile
- Kosteneinsparung beim Unternehmen bei der Anschaffung mobiler Endgeräte
- BYOD-Geräte in der Regel leistungsstärker als preisgünstige Firmengeräte
- erhöht Mitarbeiterproduktivität
- steigert Mitarbeiterzufriedenheit
- erleichtert Remote Work, Home Office, Mobiles Arbeiten
BYOD – Nachteile
- hohe IT-Aufwände durch heterogenes Software- und Hardware-Line-up
- IT-Sicherheitsaspekte (Datenlecks, Schadsoftware, Security-Breaches)
- Datensicherheit (Wirtschaftsspionage, Hacker, Datenverlust)
- Datenschutzprobleme (DSGVO, Trennung beruflicher und privater Daten, Fernüberwachung u.v.m.)
- Rechtslage bei Nutzung unklar, wenn keine ausdrückliche Nutzungsvereinbarung existiert
- Urheberrechtsverletzungen durch fehlende Software-Lizenzen notwendig
- Usability/Akzeptanz niedrig, wenn etwa das Privatgerät dem IT-Administrator überlassen werden muss
- Gefahr von Datensilos
- im schlimmsten Fall Kontrollverlust über Client-Landschaft des Unternehmens
Eine umfassende Analyse der Risikofaktoren finden Sie übrigens in unserem Blogartikel über BYOD-Risiken.
Ist BYOD alternativlos?
Nein, ist es nicht.
Mit „Choose your own Device“ haben Unternehmen die Möglichkeit, Firmenhandys rechtssicher und mit wenig IT-Aufwand einzusetzen und sich trotzdem die hohen Investitionskoten zu sparen. Grundlage hierfür ist eine Firmenhandy-Langzeitmiete.
Neben den Vorteilen DSGVO-Konformität, Mobile Device Management und einem kostenlosen Austauschservice im Fall eines Defekts können Unternehmen hier auch durch die Reduzierung des Anlagevermögens profitieren (Stichwort: Capex-to-Opex-Shift).
Erfahre mehr zu CYOD hier: Choose Your Own Device.