Have you ever lost your smartphone or mobile device? If the answer is yes, you’ll know how annoying it can be. You might have lost all your contact details, photos of friends and family, and messages with important information in them. When most people lose a phone, they simply replace it and start all over again.
However, imagine that the lost device was one you used for work purposes. Suddenly, that lost information becomes a bit more crucial. It could be sensitive data about your company or even staff members. This is where remote-wiping comes into play. What is a remote wipe? And how can you use it to ensure sensitive data doesn’t fall into the wrong hands?
What is remote wipe?
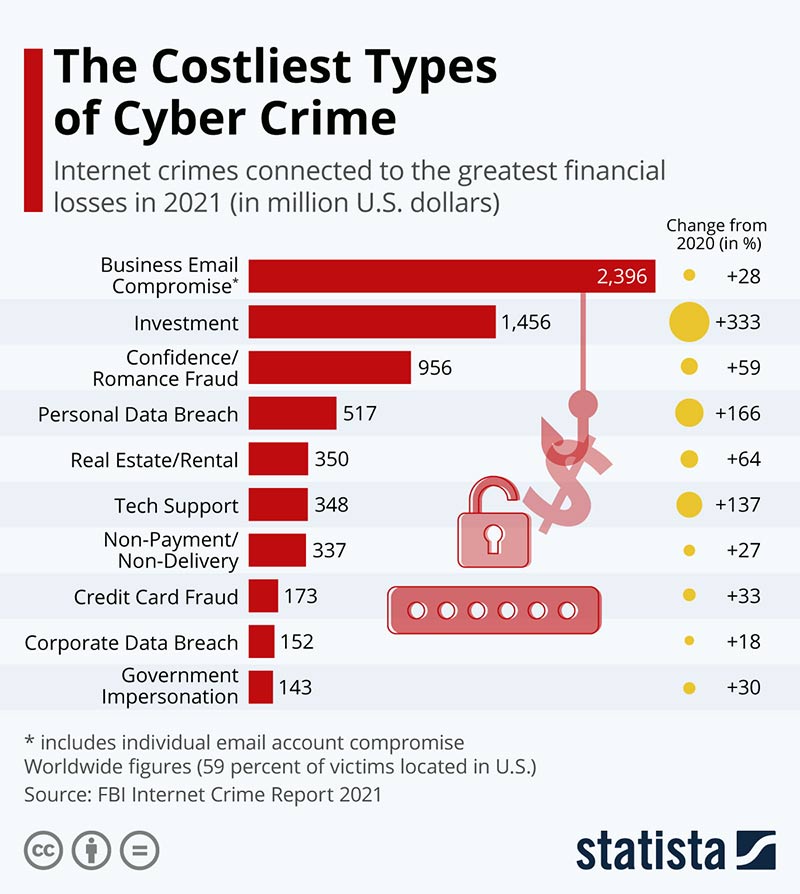
Data breaches can happen in a number of ways and can be very costly for the organization involved. In fact, the average cost of data breaches to US businesses was $9.48 million in 2023. We tend to think of data breaches as being targeted attacks by cybercriminals. But they can also happen as a result of lost or stolen mobile devices that contain sensitive information.
For example, say you have responsibility for the processing of payroll in your business. You keep a lot of the information for this on your tablet or other device. But that device is then lost or stolen. If your device falls into the wrong hands, then cybercriminals may be able to access a lot of sensitive data. This is where you would turn to the experts in your IT team.
IT admins can use an MDM (mobile device management) solution to send a command to your device that can erase all the data stored on it. Mobile security is crucial in today’s world and this means that not only is any and all data removed from the lost device, but you are thus protecting your organization from both data being compromised and a possible data breach occurring.
How does a remote wipe work?
The first thing to note is that different devices have different mechanisms in order to facilitate a remote wipe. In most cases, the device will have some form of third-party MDM solution installed on it. Your IT admins or dedicated professional can then communicate with the MDM solution and wipe some or all of the data contained on your device.

Mobile security is crucial in today’s world.
Some people may use a device for both personal and business purposes. In that case, the IT staff may perform a remote wipe that only erases certain data on the phone. So, for example, they may wipe any folders pertaining to time management software while leaving personal content such as messages and photos.
The other option they have is to permanently wipe all data on the mobile device if it contains multiple folders of sensitive data. Some employees use their devices for a lot of business-related purposes. Then it can be better to be safe than sorry and just wipe the device completely.
What does a remote wipe require?
It’s not just a case of simply pressing a button and the wipe is completed. There are certain ‘conditions’ that need to be in place in order for your IT team to perform a successful wipe.
1. Power
For a remote wipe to happen, a command is sent wirelessly to your mobile device. In order for that to happen, your lost or stolen device has to be switched on. And it has to be connected to a network. This could be a traditional PBX network or a cloud calling network such as that offered by Vonage. If the person that finds the device—or stole it—removes the sim card, then it will be impossible to wipe.
If your device is lost or stolen, you should immediately notify your IT team. The quicker they know the device is missing, then the higher the chance they can perform a remote wipe. That said, in some cases there is remote wipe software that can help even if a device is offline. These solutions can lock a device if it doesn’t connect to a network for a predetermined period.
Another advantage of these solutions is that they add protection against other threats to a lost or stolen device such as IMEI tempering, firmware, or binary editing. Does your device contain a lot of sensitive data such as Paylocity enterprise payroll information? Then it may be worth speaking to your IT team to have more advanced wipe options installed.

If your device is lost or stolen, you should immediately notify your IT team.
2. Different options
Modern mobile devices usually have a range of options that allow for remote wipes. In some cases, the remote wipe will only target any company-related data and applications. It will leave personal data and files untouched. In other cases, a complete wipe will return your device back to factory settings.
If you use your device for both business and personal reasons, it’s likely you have different profiles set up for your phone. When a device has a container setup, then your IT team may choose to only delete your work profile. Since that is the one that will most likely contain any sensitive information.
The other scenario to consider is when someone leaves your organization. Your rates of staff turnover may vary greatly. But you will still be concerned if an employee leaves and you know they may still have company data on their device. In those cases, it makes perfect sense to be able to only delete all the data that relates to your business.
If a phone has been lost rather than stolen, some solutions allow you to lock up a device so that no data can be accessed. They also allow your IT team to send a customized message to the device’s lock screen. The message contains a phone number to call if the phone is found and possibly even details of any reward offered for its return.
3. Notify employees
Businesses take data protection very seriously. They have to consider many questions from what regulations govern their data storage to understanding what SOC 2 compliance is, and how it can add flexibility and integration capabilities to your business. This protection extends to any data that employees may store on their device. So you should advise them of the possibility of a remote wipe happening in case of loss or theft.

Employees should be aware that a remote wipe could be performed at any time if required.
If the device is one that has been provided by the business, then solutions will have been installed as a matter of course. So employees should be aware that a remote wipe could be performed at any time if required. When the organization has a BYOD (bring your own device) policy, it may require the employee to install an MDM or EMM (enterprise mobility management) solution.
In that case, you should have a very clear policy re the installation of MDM or EMM solutions. You should require your employees to sign a form that shows they accept the possibility of a remote wipe happening in the case of loss or theft of the device or even if they leave your business for whatever reason.
Your company doesn’t have MDM or EMM solutions in place? You can also choose to block that particular user’s access to any company apps they have installed on their device. While this option may not remove all data contained on the user’s device, it can ensure that a lot of sensitive information contained in any apps is protected.
Many employees may not completely like the idea of the potential to remotely wipe their device. But it all comes down to your responsibility as a business to protect any and all data. You will look at every level of data protection, from that on a domain such as domain name ai to the information contained on laptops, desktops, or mobile devices.
The takeaway
Your business will assign responsibility for protection of sensitive information not only to your IT professionals but also to individual employees. Data breaches are a very real and costly threat. You need to be sure that there is protection at every level of your business. With more and more people using mobile devices for work, remote wiping is yet another form of ensuring protection.

The remote-wipe option is an important asset to protect your company’s data.
Loss or theft of a mobile device is something that happens all too often. It may not be the fault of the employee themself. But knowing that any sensitive data can be deleted remotely can give you extra peace of mind. With a wide range of remote wipe solutions available, you should be looking at the ones that offer the highest level of ability to erase any data.
You also need to consider that there are laws and regulations that govern the storage and use of data. If a data breach does happen as a result of a stolen or lost device, then you may face monetary fines as a result. Being able to remote wipe the data stored on the device, you are protecting your business from facing punitive action for causing any data breach.