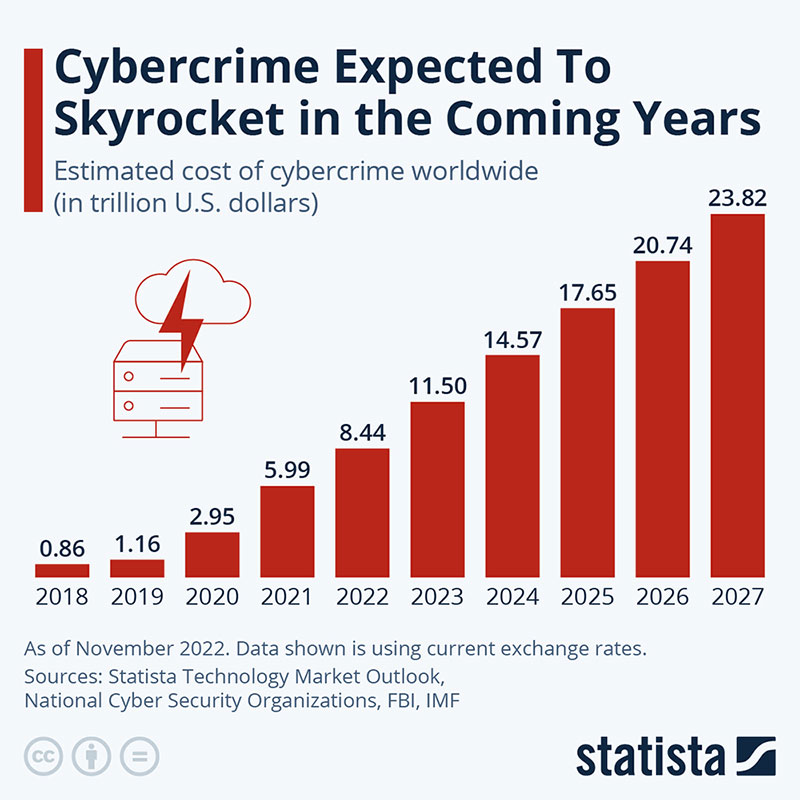
In reality, cybercrime is nothing like the almost romantic way it’s portrayed in movies. In fact, cybercrime cost businesses 7.08 trillion dollars in 2022. It is forecast to rise to 13.82 trillion dollars by 2028. This means that cybersecurity and cybersecurity training is something that every business should be taking very seriously. They should also ensure that any measures are constantly updated.
It is a challenge that particularly faces businesses who offer remote or hybrid work, where their staff may be accessing sensitive data on a wide range of devices. This means that they need to look beyond the usual in-house cybersecurity measures so that staff know what steps to take to ensure all data and information are protected.
Mobile devices and cybercrime
Your workforce may be operating remotely—or on a hybrid pattern—or it may even be the case that you have staff, such as salespeople, who spend a lot of time away from your office. This adds an extra layer of threat to potential cyber attacks. You should be aware of these threats so that you can take protective measures.
While human capital management can be a challenge when you have a scattered workforce, part of that management has to include training in cybercrime awareness and the security measures that can be used.
Some of the most common mobile threats include:
- SMiShing:
This is a very common threat with mobile devices. The cybercriminals use SMS messages to send texts that often contain fraudulent links which in turn may contain malware.
- Bluejacking:
This cyber threat uses Bluetooth to send unauthorized messages to the victim’s phone. As with SMiShing, the attacker can link you to malware or access some of your information.
- Replay attacks:
As replay attacks spy on information sent between two parties, this can be a real threat when your staff are frequently sending—and receiving—information from your ‘home base’, such as information about your payroll solutions.
- Bluesnarfing:
This is another type of cyberattack that utilizes Bluetooth technology. With this threat, the cybercriminal can copy any and all information from the target’s device without leaving any trace of what they’ve done.
- SMS spoofing:
With this cyberattack, criminals will send texts that appear to come from a legitimate source such as a government agency. If the victim is unaware of the threat, they can be duped into revealing sensitive data or downloading malware.
- Malware:
There are various ways your employees could be tricked into downloading malware to their mobile device. As well as the ones already mentioned, it could also be installed by unknowingly downloading malicious software or opening an email attachment.
How to upscale your cybersecurity training
So, you understand that cyberattacks can be a very real—and costly—threat to your organization. This is particularly the case when your staff are using a wide range of mobile devices. When it comes to human resource management, there has to be some focus on cybersecurity training. And it is something that should be revisited and updated regularly.
1. Include everyone
While you may want to focus on employees using mobile devices, any cybersecurity training—in both awareness and preventative measures—should include the entire organization. This avoids any group thinking they are the risk. But it also ensures that the whole company is receiving the same knowledge. This way, they will know the threats they face as well as how to prevent them from happening.
2. Simplicity
While cybercriminals are using increasingly sophisticated methods, your training should be simple, at least at first. It is likely that any training will be delivered by one of your IT team or even your CTO. You don’t want to leave non-technical staff bewildered by the use of jargon. When jargon has to be used, it should be explained in terms anyone can understand.
3. Content vs context
There is no point in delivering cybersecurity content to your staff if they have no idea of the context of the relevant threat. For example, if you’re delivering training on how to prevent threats to mobile devices, show them how an attack such as Bluesnarfing could capture information during exchanges between staff. These exchanges could e.g. regard a process to hire backend developers. Showing real life examples of what various threats can actually do aids with understanding.
4. Keep content relevant
Focusing on issues that are not really a threat to your organization is pointless. Your IT team should conduct a security audit that identifies your staff’s main vulnerabilities. When you create training content, it should then focus on what those vulnerabilities are and what steps employees (and you) can take to protect against those weaknesses. And you should also consider factors like the skills and expertise available in your talent pool. (What is a talent pool?)

5. Structure training to suit employees
You have employees working remotely or in a hybrid pattern? Then a rigid training schedule is not going to work well. Segmenting your workforce into different groups means that training can be delivered on days and at times that suit them. Segmentation also means that any simulations of cyberattacks, such as phishing, won’t overload your IT and/or support team.
6. Get feedback
You use feedback in different areas of your business, e.g. from using Vonage call tracking software to collect data to customer satisfaction surveys to measure customer happiness. It should be the same with cybersecurity training. Listen to what your staff say, both about the training itself and about particular threats or issues they don’t fully understand.
7. Use data and statistics
It’s important that your staff understand just how much of a threat cyberattacks can be. Your training should be underpinned with relevant data and/or statistics that show just how real it is and how it can be caused by the simplest of mistakes. Examples such as the average cost of a data breach in 2023 being 9.48 million dollars can come as a real surprise to many.

8. Train your IT team first
As your IT team will likely be leading any training as well as implementing any new security measures, you need to be sure that they are fully aware of all scenarios. Before you begin training your workforce, it can be helpful to have your IT team undergo training on cybersecurity risk assessment services. This will make it easier for them to identify threats and to construct a training program that has the most benefits.
9. Stay up to date
Your cybersecurity training should not be a one-off exercise. Cybercriminals are constantly updating their methods of attack and coming up with increasingly sophisticated ways to steal your data or information. Your IT team—or dedicated cybersecurity staff—should be staying abreast of any new threats (or changes to existing ones) and notifying all employees of any new measures that need to be taken.
Data Loss Prevention (DLP) software is one way teams can easily protect themselves from emerging threats. DLP solutions meet regulatory compliance requirements that strengthen the company’s security posture and are regularly audited for vulnerabilities.
10. Use technology
While your IT staff can teach employees how best to prevent cyberattacks, technology can play a major role too. Have your IT/cybersecurity team identify what technology may best help your organization, especially when it comes to protecting mobile devices.

Some of the tech that can help in this area includes:
- Artificial intelligence (AI) and machine learning (ML):
Systems that use AI and ML can be a major aid in combating cybercrime. As they can analyze enormous amounts of data quickly, they can identify threat patterns and even forecast types of attacks, allowing your team to deal with them more proactively.
- Behavioral patterns:
Around 81 percent of data breaches are caused by either weak passwords or poor password security. While this is something you would normally address directly to staff, using ML biometrics technology can help analyze and identify normal user patterns and can quickly spot anything abnormal.
- Cloud technology:
If you have remote, mobile, or hybrid workers, then it’s likely that you’re using cloud computing and storage. While useful to your workforce, it does mean you face many new security challenges. Cloud security tech and measures such as MFA (multi-factor authentication), encryption of data, and authorized access can mitigate some of those risks.
- IoT security:
Smartphones and other mobile devices are IoT (internet of things) devices. The definition can also extend to other non-standard computing hardware that your remote workers may be using. Of course, that extended use also means more susceptibility to cyberattacks. Using technology to increase the level of encryption and monitor usage can help prevent those attacks.
The takeaway

Cybercrime is a very real threat and one that could potentially cost your business millions of dollars. It can be hard enough to have efficient in-house cybersecurity tactics. But if you have remote or mobile workers using a multitude of mobile devices, then those threats are multiplied. You need to first identify every vulnerability that may leave you exposed and then seek to close those vulnerabilities.
Cybersecurity training should be an exercise that is regularly revisited. Just as the cybercriminals come up with new methods and threats, so should your security experts be looking for ways to combat every threat you face. Ensuring that cybersecurity training for every employee is constantly updated and upscaled when needed can give you more peace of mind.