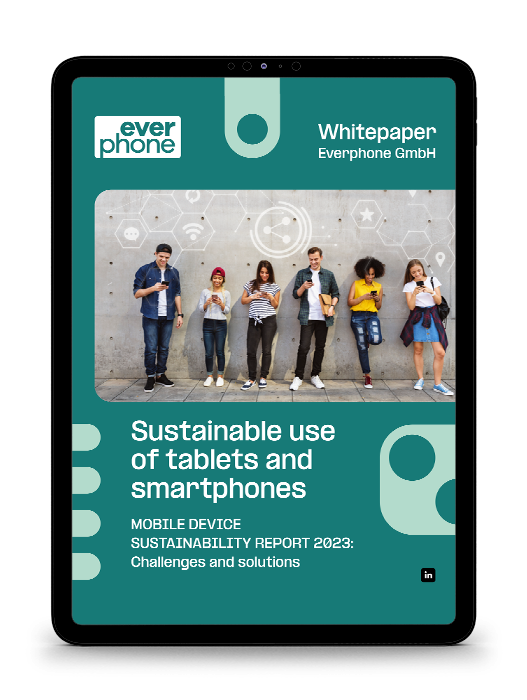
Already, your organization likely uses a significant number of different devices, on and off premises. Think desktop computers, laptops, smartphones, tablets, and all kinds of virtual solutions and domains on the company network. And this number is only going to increase as the business continues to expand.
The problem with using so many devices is that it means an equally high number of endpoints, and each endpoint is a potential entry point for cyber attackers. Endpoint security is crucial to eliminating cybercrime.
It might seem intuitive to use a different solution to manage security on different types of devices. But is that the right strategy?
Unified endpoint management (UEM) allows security teams to monitor and manage all endpoints and devices on the network from a single tool, ensuring consistency in company-wide security measures.
This article will explain exactly what UEM means in simple terms, highlighting its uses and benefits in ensuring endpoint security.
What is UEM?
UEM is an umbrella term for any platform or software which offers a single interface to control and manage all of an organization’s endpoint devices. That means desktops, laptops, mobile devices, tablets, wearables and more are all secured from a single console, regardless of operating system or location.
This unified approach helps improve security as it simplifies the process of protecting multiple endpoints, reduces administrative complexity, and allows updates and security policies to be applied consistently across various devices.
A typical solution will also have features like advanced threat detection, mitigation, and remediation capabilities, as well as remote control options and patch management.
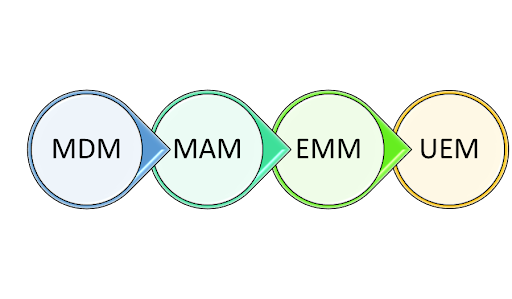
UEM is an evolution of mobile device management (MDM) and enterprise mobility management (EMM) combined with traditional client management tools. While relatively new, UEM technology has become increasingly popular as more companies transition to hybrid or remote work.
The evolution of UEM
It’s easy to get confused given the abundance of device management solutions out there–especially as UEM, MDM, and EMM are often misunderstood and used interchangeably. Although some features overlap, these solutions offer different things.
In fact, each is an extension of the one before. UEM, then, is the latest in a series of mobile security management tools spanning the last two decades. Each one emerged and evolved in response to changing relationships between organizations, employees, mobile devices, and working styles.
To understand UEM, let’s briefly cover the similar tools which came before.
MDM (mobile device management)
First, there’s mobile device management (or MDM). MDM tools were developed in response to the first mobile devices being introduced to the workplace. These tended to be company-owned. With MDM tools, administrators had total control over all device features, therefore ensuring security and connectivity.
MAM (mobile application management)
As smartphones increased in popularity, a new solution was needed. Employees became less willing to carry both a personal and a corporate device–instead, they preferred to use personal devices in the office.
Thus: the advent of BYOD (bring your own device) culture. With this shift came the difficulty of working out private use and work phone agreements.
IT administrators could not demand total control of these personal phones as they had with company-owned devices. Employees did not want to surrender their personal data. Even handing over your private phone to an IT team colleague for the installation of corporate software is a no-go nowadays. Still, companies need to be able to secure corporate assets.
Mobile application management (MAM) was developed to facilitate this balancing act. Rather than controlling all functions of a device, it focused on app management, corporate applications and data. Without gaining access to private information, administrators were able to exert just enough control to ensure security for the company.
EMM (enterprise mobility management)
Despite its advances, MAM solutions could not keep up with BYOD-related security issues, as employees were downloading new apps faster than MAM could scan them.
In response, vendors combined aspects of MDM with MAM with other related tools. The result, enterprise mobility management (EMM) suites, provided the corporate data security of MDM along with the employee autonomy of MAM. EMM allowed for management and security control over all devices used outside of the office – not just smartphones but also off-site laptops and PCs.
UEM (unified endpoint management)
While EMM suites were an improvement on what came before, there was still one issue: they couldn’t manage on-site devices. This meant that IT administrators required different tools to manage off-site and on-site device security – leading to unnecessary confusion, compared to if there were one comprehensive solution that could handle both.
This is where unified endpoint management comes in. UEM was created by software developers by merging features of traditional EMM with existing client management tools, resulting in one solution to safeguard all endpoints within an organization, whether on-site or off.
UEM is good not only for securing devices but also assets. For example, a company operating in Australia may manage their online presence with a .com.au Domain name.

How does UEM improve endpoint security?
Unified endpoint management platforms take an all-encompassing approach to security. From a central dashboard, administrators can perform or automate management and security tasks for any or all devices on the network.
Enrolling and provisioning new devices
UEM solutions provide a portal where users can self-enroll and have their devices provisioned automatically, thus reducing the administrative burden of BYOD. Additionally, UEM automatically enforces enrollment and provisioning for any new device attempting to connect to the company network.
Applying and enforcing security policies
UEM enables admins to deliver consistent policies across all devices from one interface. For example, admins might specify multi-factor authentication, password length and complexity, mobile security, or data encryption methods. The ability to enforce these standards with a single tool significantly reduces manual work for security staff.
Pushing patches and updates
You can ensure constant monitoring as UEM scans endpoints for software vulnerabilities, software updates, and other firmware issues. UEM can automatically push patches where required, helping organizations remove vulnerabilities, minimise intrusion risks, and keep software up-to-date.
Controlling applications
Using UEM, employers can approve or prohibit the use of specific apps and prevent unauthorized applications from accessing enterprise data. Many UEM tools allow the creation of an app store where users can only install enterprise-approved apps onto their devices.

Categorizing data
BYOD policies make it difficult to distinguish between personal information and corporate data on employee devices. With UEM platforms, however, it becomes easier to isolate the different data types and ensure the necessary protection for each category.
Threat hunting and response
Integration with endpoint detection resource (EDR) systems allows UEM to detect abnormal behavioural patterns. From these patterns, UEM tools can identify complex potential threats or ongoing harm and then trigger other security tools to take action.
Wiping and/or locking lost, stolen, or end-of-lifecycle devices
It’s important for businesses to be able to protect against unauthorized network access and prevent sensitive data from falling into the wrong hands. If a company phone is stolen, for example, you need to act fast.
UEM allows administrators to remotely decommission devices which are lost or stolen so that they do not pose any threat. Or, if a device has reached the end of its lifecycle, it can be reset for continued personal use.
What are the benefits of UEM?
Enhanced IT security
A centralized approach to security makes it easier to monitor suspicious activities across all devices than to enforce relevant security policies at various levels. UEM therefore helps IT admins to ensure a strict defense against all threats.
UEM’s non-negotiable security policies are especially useful to companies that want to enforce maximum endpoint security with no loopholes for data breaches.
Increased visibility
UEM promotes visibility across all endpoint devices and connected networks, as everything is being managed from the same interface. Continuous visibility is a necessary element of any comprehensive security strategy. It allows enterprises to monitor data uses, inventory, and vulnerabilities, while also keeping security teams alert to possible threats.
Enhanced online presence
UEM’s capabilities extend to online presence management. Businesses can effortlessly monitor the status of their various domain names, from registration and renewals to DNS configurations. This enables the company to maintain a consistent and accessible online presence, with added credibility from Only Domains domain names.
Convenient single-pane architecture
Companies realize that in any digital-first workplace, employees need critical data at their fingertips for swift and informed decision-making. Managing multiple desktop and mobile devices with different sources of truth works against this.
UEM collects historical data with a single dashboard, console, or “pane” spanning the whole stack of device monitors. It avoids complicated integration that may otherwise be needed to retrieve cross-platform data and also provides real-time visibility into assets via descriptive dashboards. Single-pane architecture therefore facilitates better business decisions, backed up by easily accessible data.
Furthermore, having company data organized and accessible will always be an asset down the line. For example, in the event of a merger or acquisition, it will be easier to structure your data room if everything is visible from one console.
Device agnosticism
UEM does not limit employees to a certain type of device. Instead, they can use whichever device they are most comfortable with–from corporate-owned to personally-owned smartphones, tablets, laptops or PCs. By not restricting the devices employees work with, you allow them to get straight into productivity rather than training on an unfamiliar piece of tech. As well as improving the employee experience, this increase in morale and efficiency also benefits the business as a whole.
Reduced IT management costs
So, how does this impact the bottom line? UEM allows you to automate several IT processes and tasks, such as endpoint auditing, provisioning, and data loss prevention. This minimizes IT overhead costs and hardware expenses.
Final thoughts
In summary, it seems that unified endpoint management is the next step for businesses looking to secure and manage their various devices and assets via one coherent platform.